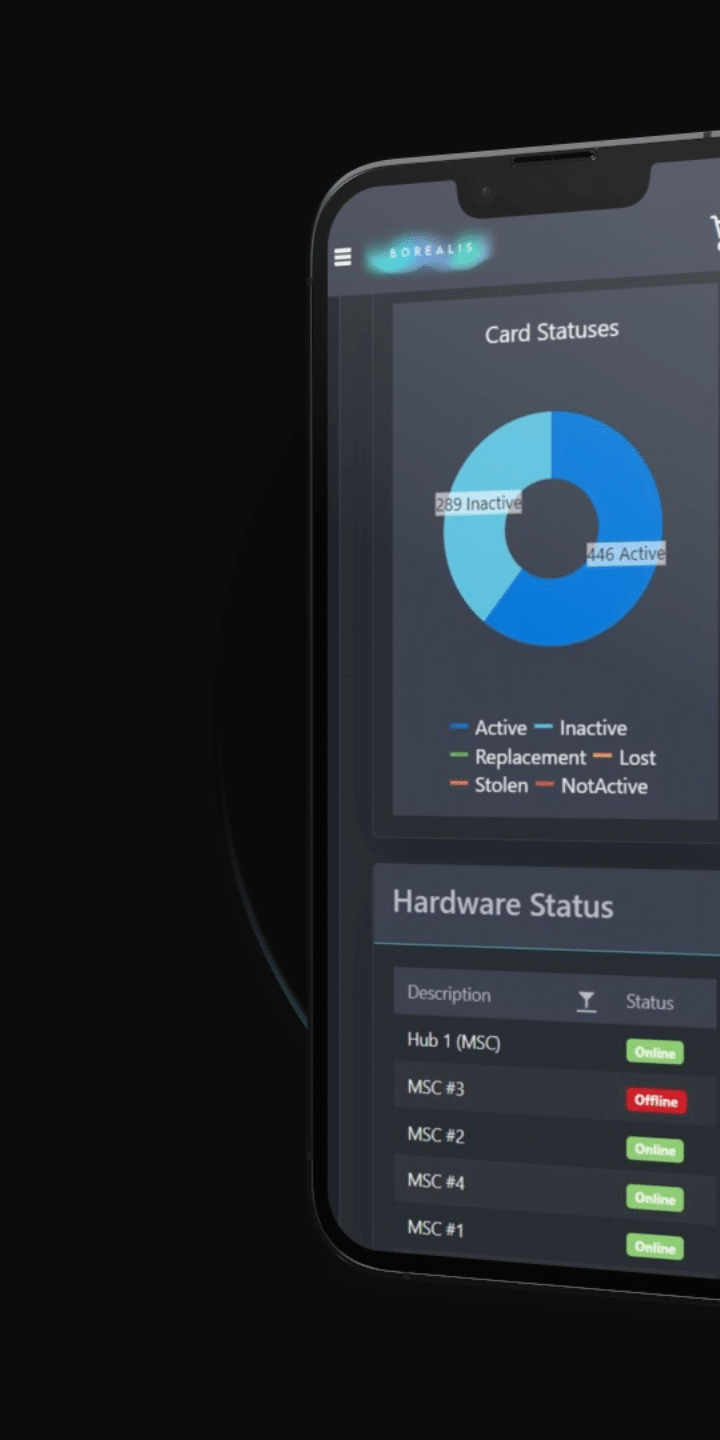
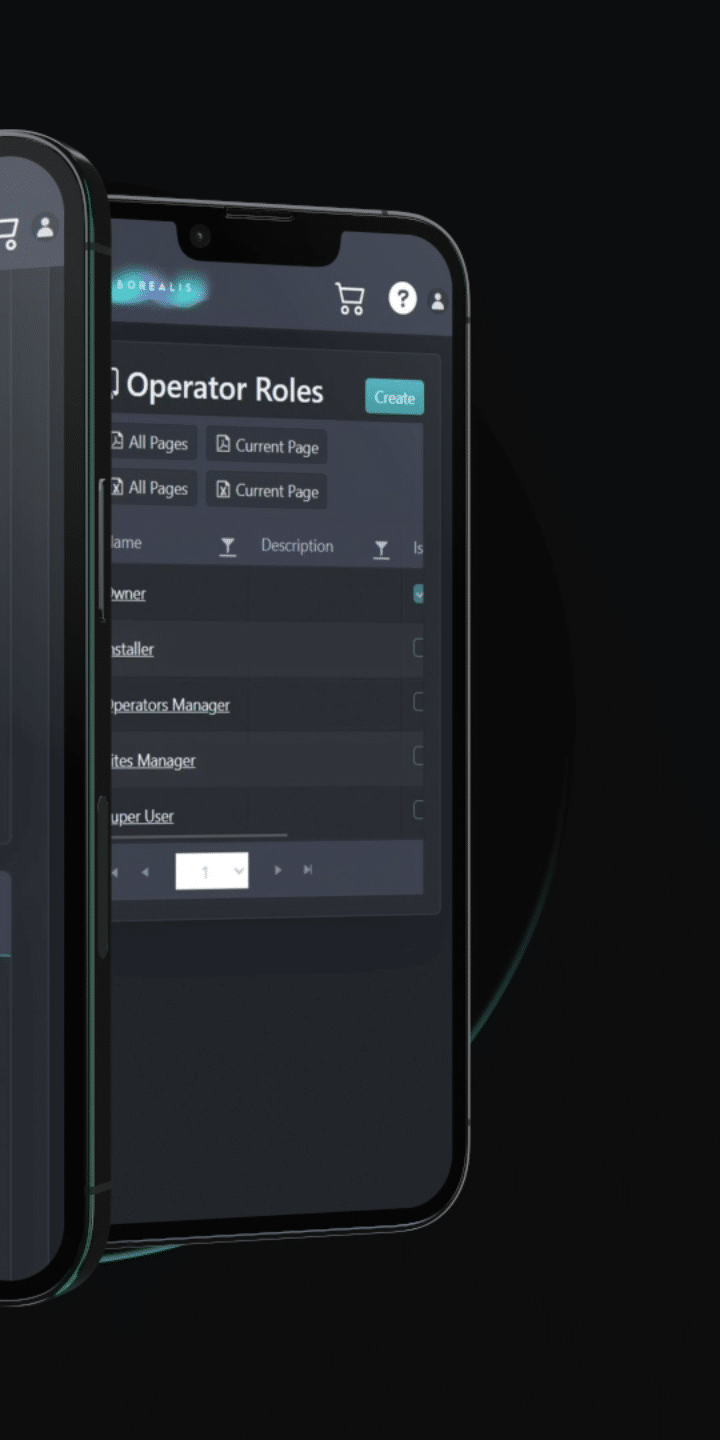
Streamlining Experiences
Mobile credentials play a pivotal role in the access control ecosystem.
Access control systems are an essential part of most modern businesses and organizations. They provide security and peace of mind by restricting access to specific areas, equipment, and information. Traditionally, access control systems relied on physical access cards or key fobs to authenticate users and grant access. However, with the rise of smartphones, mobile credentials are rapidly replacing traditional physical access cards, and for good reason, too!
Mobile credentials leverage smartphones to provide secure authentication and facilitate the integration of access control with digital wallets. They offer several advantages, including robust encryption and multi-factor authentication, making smartphones one of the most secure forms of identification. These credentials are rapidly issued to new employees or tenants, regardless of their physical presence. They can be securely pushed to the recipient from anywhere worldwide, as long as there is Internet connectivity.
One of the main benefits of mobile credentials is their convenience. Users can easily access their mobile credentials through their smartphones, eliminating the need for physical access cards or key fobs. This makes it easier for businesses to manage access control, as they can issue and revoke mobile credentials remotely. This is especially important in today’s increasingly mobile workforce, where employees often move between locations.
Advantages of Mobile Credentials
There are a host of advantages to using mobile credentials to enhance or replace traditional identification methods. These include:

Near real-time issuance of credentials to new employees or tenants, irrespective of whether they are present. When coupled with a cloud-based Access Control SaaS, a mobile credential can be pushed out to the recipient from anywhere in the world, as long as there is Internet connectivity.
Built-in multi-factor authentication. When using a mobile credential, modern smartphones already provide multi-factor login; for instance, a fingerprint, facial scan, or PIN code to unlock the phone before pushing the mobile credential from the phone to the reader.
Mobile phones are the most “hack” resistant ID devices a user can carry due to the built-in, robust encryption.
Often seamlessly integrated as part of a multi-function app and a SaaS offering, particularly for multi-family and multi-tenant business applications.
There is much better enforcement of identification (meaning someone else isn’t using an ID credential). It’s far less convenient to hand someone a phone for long-term access rights than to provide someone with an ID card or tag.
It provides an excellent opportunity for the Installer to claw back credential revenue lost to some OEMs or Card Bureaus selling physical credentials directly to the End User.
Access Using Mobile Credentials
Using your smartphone to gain entry
Mobile credentials also allow better enforcement of identification, making it more challenging to share access rights with unauthorized individuals. This helps to prevent security breaches, as it ensures that only authorized individuals are granted access to restricted areas or information. This is particularly important for businesses that deal with sensitive information or operate in high-security environments.
Although the fees imposed by Apple and Google for access control usage of mobile credentials may seem challenging for some businesses, it is important to remember the many benefits that mobile credentials offer. With mobile credentials, businesses can experience improved security, enhanced convenience, and cost savings long-term. Despite the fees, the adoption of mobile credentials is still a smart investment that can provide businesses with a competitive edge and streamline their operations.
Mobile credentials do, however, offer an excellent opportunity for security installers to increase their recurring revenue by providing the credential on a SaaS product such as Borealis. This replaces a one-time sale of a physical credential with a software-based product with a recurring revenue stream. This can be a significant source of revenue for security installers, as they can charge a recurring fee for each user who accesses the system through their mobile credential.
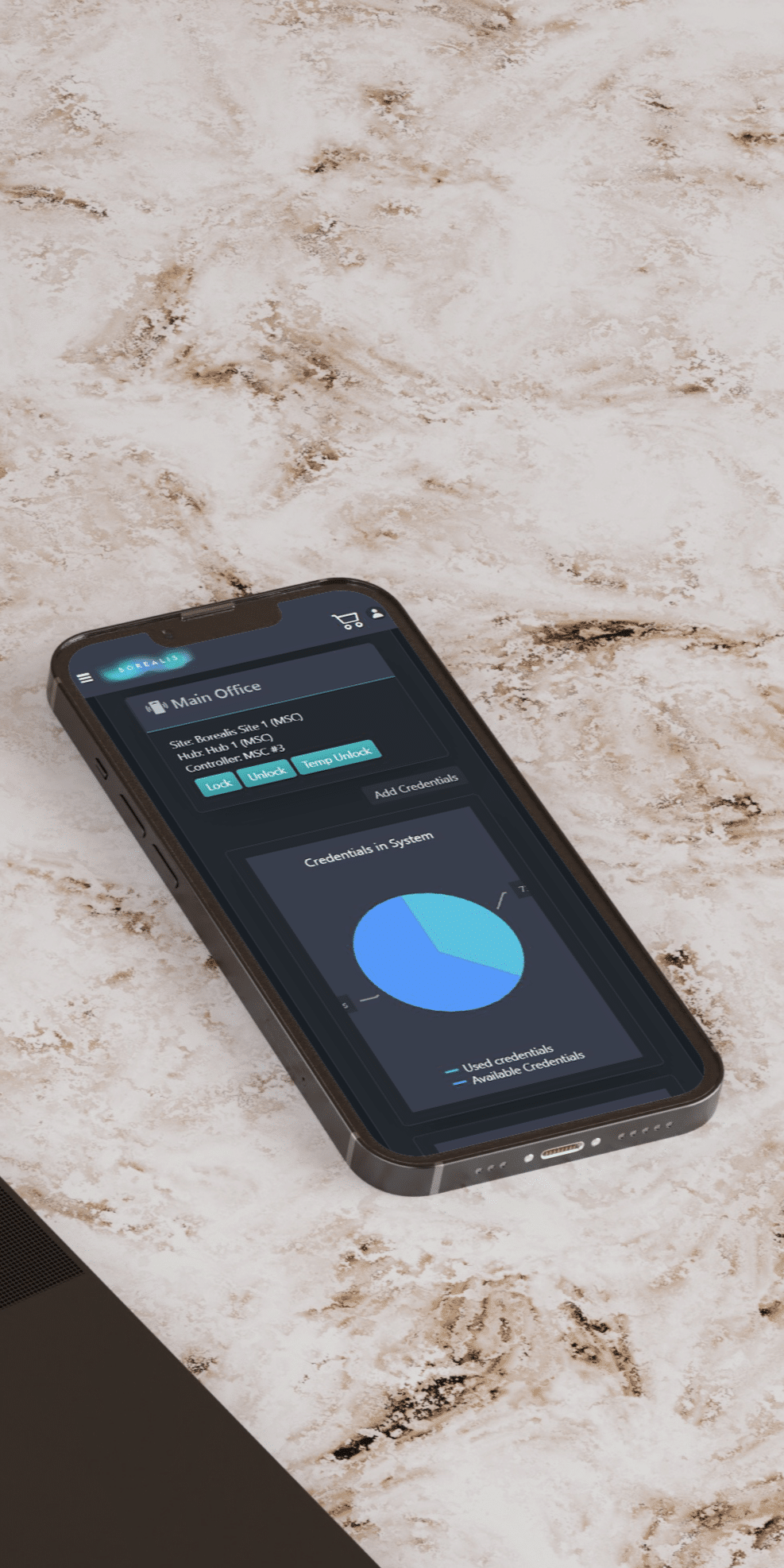

Mobile credentials are also highly scalable, making them an ideal solution for businesses of all sizes. They can be rapidly issued to new employees or tenants, regardless of their physical presence. They can be securely pushed to the recipient from anywhere worldwide, as long as there is Internet connectivity. This makes it easy for businesses to scale their access control systems as their needs evolve.
In addition to scalability, mobile credentials also offer greater flexibility than traditional access cards. This is because they can be easily customized to meet the needs of individuals or groups of users and can be configured to grant access to specific areas or equipment. Additionally, this level of customization is not possible with traditional access cards, which are typically limited to a single level of access.
Mobile credentials are also incredibly secure. They leverage the latest encryption and multi-factor authentication technologies to ensure that only authorized users are granted access. This makes them ideal for businesses that deal with sensitive information or operate in high-security environments. Because they are stored on smartphones, they are less susceptible to loss or theft than traditional physical access cards.
In Conclusion
Finally, mobile credentials offer a more streamlined and efficient access control experience for users. With traditional access cards, users must often swipe their card or fob multiple times to gain access to different areas or equipment. With mobile credentials, users can easily access all of their credentials through their smartphone, eliminating the need for multiple cards or fobs. This can save time and reduce frustration for users while also improving the overall user experience.
In conclusion, mobile credentials, when used in conjunction with cloud-based access control offerings, provide security installers with the best opportunity to transform their revenue model from one-time sales to recurring software charges. While there are some upfront costs associated with using mobile credentials, the long-term benefits in terms of convenience, security, and scalability make them an excellent investment for businesses of all sizes. By leveraging the latest encryption and multi-factor authentication technologies, businesses can ensure that only authorized users are granted access while also streamlining the access control experience for users.