Everything You Need To Know About Cloud Based Access Control
What is Cloud-Based Access Control?
Cloud-based access control is a type of security system that uses cloud computing technology to remotely manage access permissions and authentications. This allows organizations to securely control who has access to their valuable resources, regardless of physical location or device. It also provides an efficient way to manage multiple users’ access rights across various networks and environments. By leveraging cloud technology, cloud-based access control systems enable organizations to quickly and easily manage access rights from anywhere. They also offer the ability to customize access permissions and authentication requirements based on user type or role, ensuring that only authorized personnel have access to secured areas.
With cloud-based access control, organizations can improve their security posture without sacrificing convenience or accessibility. By streamlining access control, cloud-based access control systems can reduce the time and cost associated with managing multiple users’ credentials across numerous networks. In addition, they also provide real-time visibility and insights into access activity to help organizations identify potential threats and quickly respond to them. Cloud-based access control is an essential component of any organization’s security strategy. By taking a proactive approach to access control, organizations can ensure their valuable resources remain secure and protected from unauthorized personnel.
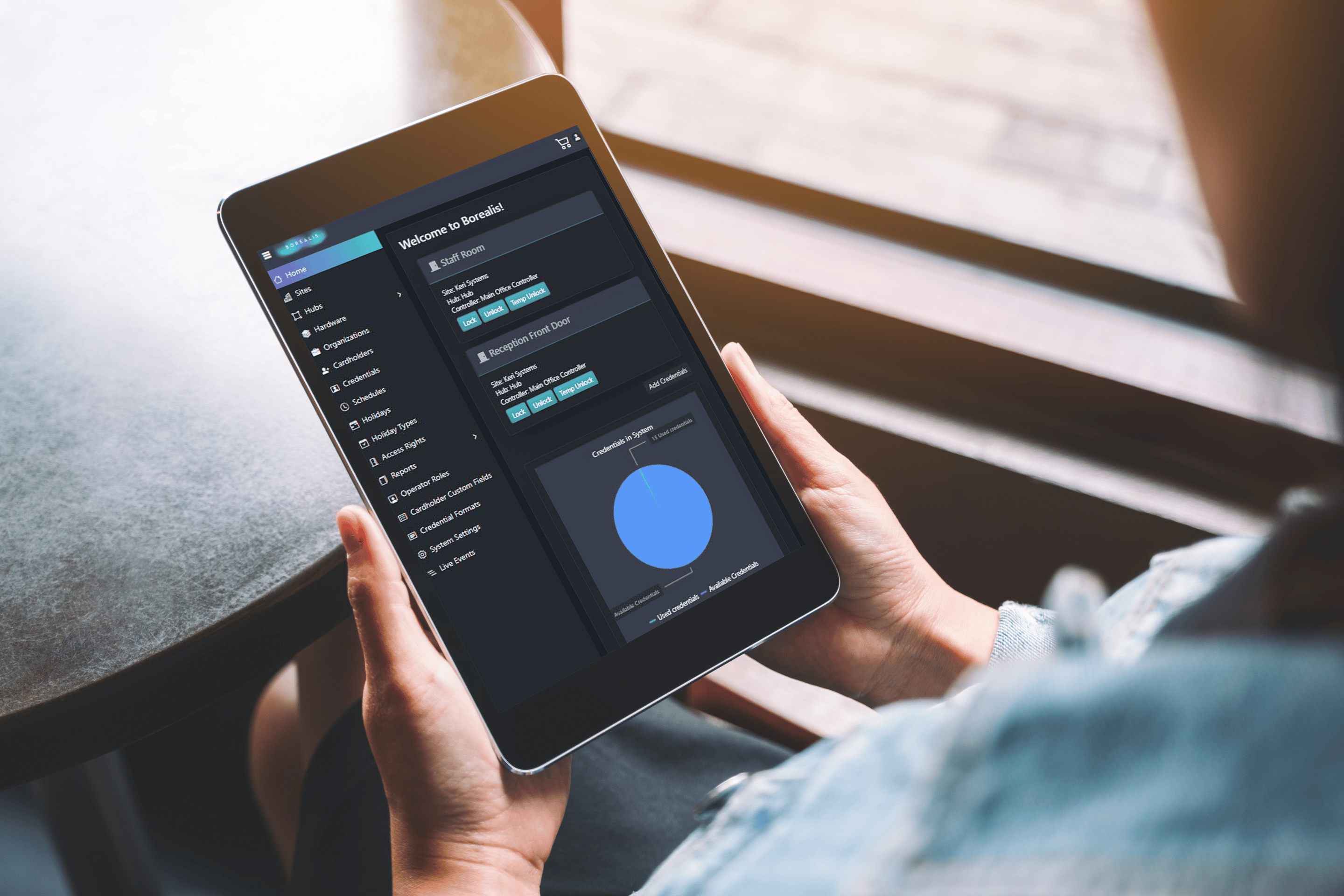
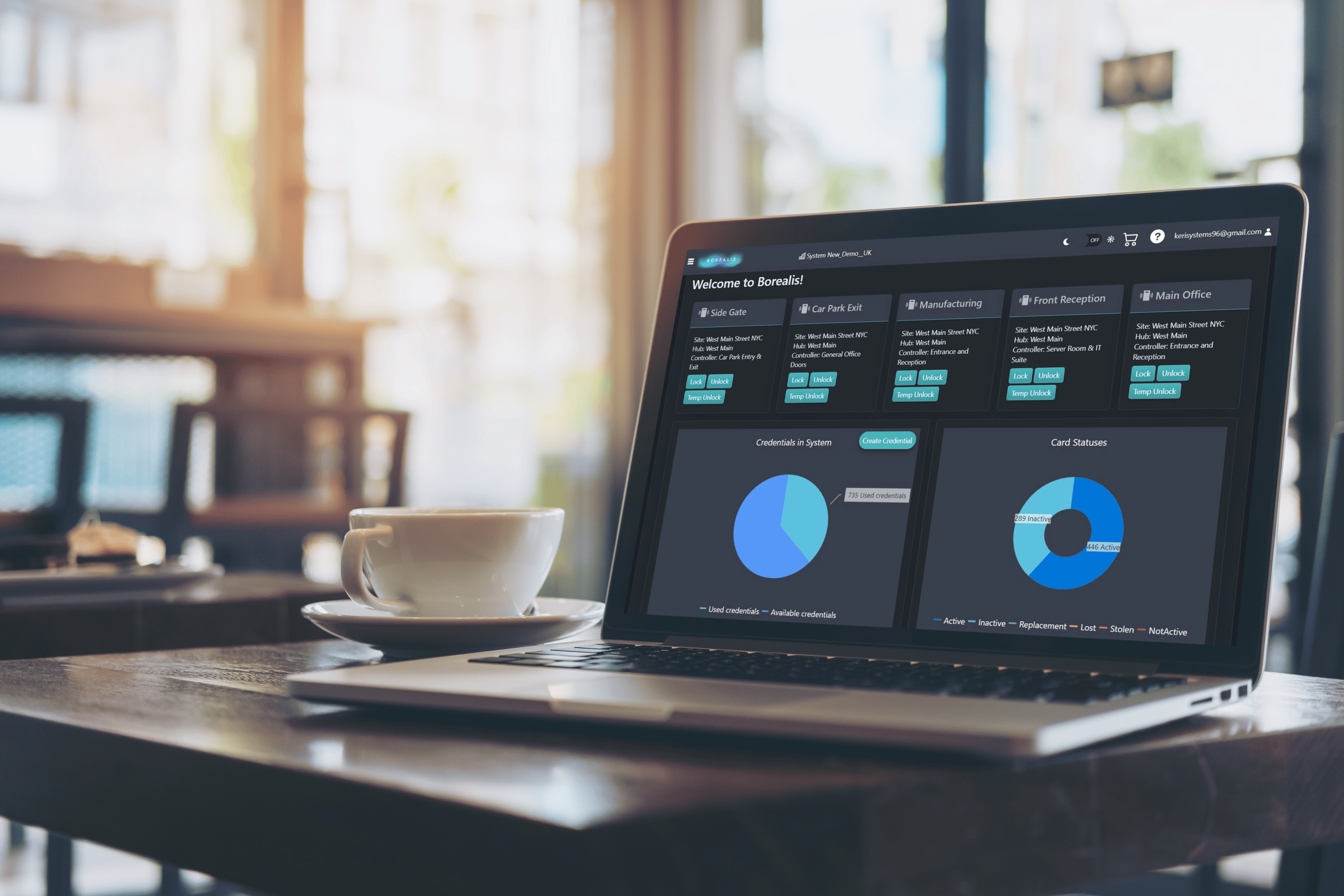
Keri offers a cloud platform ‘Borealis’ that is designed to work on multiple devices, and offers all of the benefits of a cloud based solution, granting the ability to manage and monitor your access control solution from anywhere at any time by using an internet-enabled browser. You can always keep track of your security by viewing events within your building in real-time, our cloud solution enhances the security management experience by simplifying previously complicated tasks, delivering global accessibility, scalability and convenience.
- With Borealis, you don’t need to worry about disk space, software maintenance, or backup storage as your data is stored on a flexible and secure cloud server that can scale up and down with your system size.
- Accessed from anywhere with just an internet connection and a browser – including smart devices.
- Borealis utilizes a browser-based management suite, which is responsive to all devices, there is no software to install or maintain on your computer. As it’s a cloud service, we ensure you are always on the latest version.
- Borealis has been designed for precise scalability across multiple device types, to make managing your access control solution easier than ever.
- Guaranteed ‘up’ time of 99.99%

Features of Cloud-Based Access Control
Cloud-based access control systems provide a wide range of features and benefits, making them an ideal choice for companies looking to increase security while reducing costs.
One key feature of cloud-based access control is the ability to remotely manage access permissions. This eliminates the need for someone to be physically present in order to grant or deny access. Access permissions can be set up, modified, or disabled from anywhere with an internet connection. This allows companies to control access to sensitive areas without having to invest in additional onsite personnel or hardware.
Another feature of cloud-based access control systems is the ability to customize user roles and privileges across multiple sites. This eliminates the need for complex access control lists or manual processes. Different user roles can be assigned different privileges, such as the ability to access specific areas or certain types of resources. This level of compartmentalization makes it easier to ensure that only authorized personnel have access to secure areas.
Cloud-based access control systems also offer robust audit and reporting functionality, which ensures compliance with industry regulations. Companies can monitor who is accessing which areas in real-time and review detailed audit logs of past activity. This helps ensure that only authorized personnel are accessing restricted areas, while also providing evidence of compliance with regulatory standards.
These features make cloud-based access control systems highly versatile and secure solutions for companies looking to increase their security without increasing their costs. With real-time access control, customizable user roles, and detailed audit reporting, cloud-based access control can help companies protect their assets while adhering to industry standards.
Cloud-Based Security Vs. Traditional
Cloud-based security is quickly becoming the preferred method for protecting businesses from cyber-attacks and data breaches. Cloud-based security solutions offer significant advantages over traditional approaches, such as improved scalability and flexibility, reduced cost of ownership, better access control, enhanced visibility and monitoring capabilities, quicker response times to threats, and greater protection against malicious attacks.
Unlike traditional security solutions, cloud-based solutions can be easily configured to meet the changing needs of businesses. These solutions also allow for more efficient management of access control and user authentication, providing better visibility into who is accessing secure areas and how they are using it. Additionally, since cloud-based solutions are hosted in remote data centers, they provide better protection against physical threats such as device theft and data breach.
Cloud-based security solutions also offer improved response times to potential threats. By storing information in remote cloud servers, the cloud host can quickly detect suspicious activity and take corrective action before a data breach occurs. Some cloud-based security solutions even allow for automated response to threats, making it easier for businesses to stay ahead of their security needs.
Finally, cloud-based security solutions provide better overall value when compared to traditional approaches. Traditional solutions can be costly and time consuming to maintain, while cloud-based solutions are more cost effective and offer faster implementation times. Additionally, since cloud-based solutions are hosted in the cloud, they offer businesses more flexibility in terms of where their data is stored and accessed.
With the Cloud:
- Forget the headache of local servers! By hosting data on a secure, remote server, your business can save time and money—no maintenance or training required.
- The Cloud is more convenient than traditional storage methods.
- The Cloud can be more affordable than traditional storage options.
Without the Cloud:
- High costs can often be lurking beneath the surface – from ongoing maintenance to added fees for software updates and training.
- Remotely managing your system comes at a price – more complexity, and financial investment.
- Working with outdated systems can be a challenge.
Why move your access control to the Cloud:
Cloud-based access control systems can offer your business many benefits.
For instance, they can reduce costs associated with traditional on-premises systems such as hardware and software upgrades, maintenance and staffing needs. Additionally, cloud access control systems often provide improved scalability, reliability and flexibility compared to their on-premises counterparts. They also enable remote access and management, making it easier to administer security protocols from anywhere. By moving access control to the cloud, you can enjoy all of these benefits while keeping your data secure.
Access Control for Every Industry
Email Us
sales@kerisys.com
Call Us
(800) 260-5265Get A Free Quote
Tell us about your project
